December 27, 2022
by Steve Endow
On December 22, 2022, LastPass disclosed that they had discovered that an attacker had copied a backup of customer "vault data" following a cyberattack and data breach that occurred in August 2022.
Aside from the obvious bad news, I initially learned of two interesting things about LastPass that I never would have thought to consider when evaluating password managers.
1. While web site username and password values are encrypted, the URL for the web site entry is not encrypted by LastPass. I believe this poses a security risk for LastPass users.
2. Prior to 2018, LastPass used 5,000 iterations in the key derivation process. In 2018, they increased that to 100,100 iterations. Even if you don't know what key derivation iterations are, just make note of that significant change. From what I've read, older vaults were not automatically upgraded to the more secure configuration. In theory, this means that vaults created prior to the 2018 upgrade are potentially more vulnerable to brute force password cracking.
While not a technical detail, I also read about an additional concern:
LastPass did not require users to have strong(er) master passwords over time. For example, a customer who signed up in 2016 might have had a master password less than 12 characters. When LastPass increased the minimum master password length to 12 characters, existing users were not required to increase the length of their master password. So customers with weaker master passwords are potentially at higher risk of having their stolen vault accessed through brute force password cracking.
Blind Trust, No More
After learning about these details, I realized that I knew next to nothing about my password manager. I blindly assumed it safely encrypted my data, but I had never actually investigated any of the details of the security of my password manager and the company that provides the software and cloud hosting for synchronization.
I suspect I am not alone.
As a result of the LastPass breach, I have attempted to dig into the details of how several password managers actually encrypt data and their security practices. As a result of this research, I have new criteria for evaluating password managers.
You're Shopping Wrong
Many (most?) people shop for a password manager by reading "reviews" that claim to tell you "The Best Password Manager in 2022". They then read blog posts claiming to compare Password Manager A vs. Password Manager B. They show a list of "features" with green check marks and list the pricing plans.
Those sources can be helpful for understanding basic features and pricing, but in my experience, they do not tell you anything meaningful about the true security of the password managers or the companies selling them.
"But the article says they use AES! That's MILITARY GRADE encryption!"
The information provided by such articles and "reviews" should only be the first step in your search for a password manager. They are almost never comprehensive, and I suspect many are not objective--with affiliate links or other questionable marketing links.
Unwarranted Loyalty
If you've ever mentioned the name of a password manager on the Internet, you've invariably seen the proud replies:
"I use Super Crypto Vault because its the best."
"I've been using Top Secrets Manager Platinum--my whole family uses it and it's swell!"
"My company uses Mega Cipher Enterprise. It's got ALL the neat features."
And, of course, there were presumably folks who, prior to August 2022, would have chimed in with, "I love LastPass! It works great!" I'm assuming that loyalty for LastPass has faded a bit in December 2022.
While I understand the desire to like something you've used for years, that you're familiar with, and that you've trusted, I would caution you to avoid blind loyalty.
Evaluate the product based on specific criteria and objective information.
Here are my new criteria as of December 2022.
1. Does it have the features I need so that I can use it effectively?
Most of the popular commercial password managers have the features I need. Some have one or two unique features, some work slightly differently. If you actually test 3 or 4 of these password managers, you'll see that they are all very similar in functionality, and you have to choose based on one or two unique requirements or features or quirks, or perhaps a more economical subscription option.
I mention "use it effectively" because I regularly encounter people who insist that KeePass is the best password manager because it is open source. If they are technical, they might say "PBKDF2 is insecure! You should be using Argon!". But if you look into the effort required to configure KeePass to function like a modern commercial hosted password manager, it quickly becomes clear that it would be unusable for the average person.
My criteria regarding such complexity in password managers: If my wife and kids can't use it, it isn't an option for me or my company. I am willing to accept PBKDF2 with 200,000 iterations in exchange for convenience.
2. What is NOT encrypted?
When I researched the LastPass vault breach, I learned that LastPass does not encrypt web site URLs. This came as a surprise to me.
I read that the URLs are not encrypted to allow LastPass to display the logo of the web site next to each password entry.
By storing unencrypted web site URLs in vault entries, each LastPass user can be associated with every web site in their vault. I believe this poses a significant security risk to users. They are now targets for phishing, password resets, 2FA fatigue attacks, and account compromise. Since full customer contact information was also stolen in the LastPass data breach, attackers now have a comprehensive profile of every LastPass user. They could be targeted for years to come.
Based on this lesson, I want my password manager to encrypt everything I type into it. If the vault is copied during a data breach, I want it to expose as little information as possible.
I've discovered that finding an example of the actual data stored in a password vault is quite difficult. I will be researching how to find this information.
I found this thread that showed a purported example of the data from a BitWarden vault. You can see plain text metadata, but all sensitive fields appear to be encrypted.
https://www.reddit.com/r/Bitwarden/comments/zuxdwc/does_bitwarden_encrypt_all_fields/
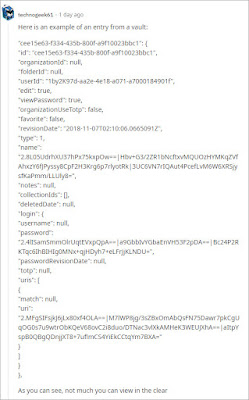 |
| BitWarden Vault Entry |
3. Encryption Algorithm and Parameters
I can understand that most people aren't familiar with encryption algorithms, and ideally, they shouldn't have to be. But after learning that LastPass previously used only 5,000 iterations for key derivation, I realized that I probably needed to pay attention to that detail when shopping for a password manager.
I tried to look for information on the encryption details for my current (old) password manager. First, it was difficult to find, which wasn't a good sign. When I finally found the "security whitepaper", I was disappointed. The whitepaper was published in October 2018. This is the first red flag--the security documentation has not been updated in 4 years.
 |
| No Cipher Mode and 4,000 iterations |
The document simply states that the "AES-256 algorithm" is used. It doesn't have any mention of CBC or GCM cipher mode. I don't necessarily care which cipher mode they use, but the fact that it isn't even mentioned in the security whitepaper concerns me. When I read the security whitepapers of other password managers, the cipher mode is explicitly and clearly documented, and some papers explain why they chose that particular cipher.
The other, larger concern was the mention of 4,000 iterations for key derivation. As of August 2016, NIST guidelines recommended a minimum of 10,000 iterations. That was 2 full years before my vendor's whitepaper was written or last updated. After reading this "security whitepaper", I knew I had to find a new password manager.
While reviewing the encryption documentation for a few password managers, I learned that 1Password and Keeper use AES-GCM, while BitWarden and Dashlane use AES-CBC. The GCM cipher mode appears to have some potential benefits, but I will need to learn more to understand why 1Password and Keeper chose CGM.
4. Documented Security Audits
Review the security audits for the password manager software and vendor. This should be easy to find in a web search. If you can't find the information easily, I would be concerned.
Examples:
https://support.1password.com/security-assessments/
https://bitwarden.com/help/is-bitwarden-audited/
https://keepass.info/help/kb/trust.html
https://www.keepersecurity.com/security.html?s=compliance
Actually read the security audits and assessments. Even if you don't understand any of the technical details, you will quickly get a feel for the nature of the audit and how comprehensive it was.
For example, skim through this "Web-based components" security report for 1Password from April-May 2022 by Recurity Labs:
https://bucket.agilebits.com/security/378.2101-Recurity_Labs-Report-B5-v1.0.pdf
Notice the "testing notes" provided by AgileBits to the security reviewer. Very impressive.
 |
| 1Password is highlighting complexities that may be vulnerable |
Compare the security audit information from 1Password, BitWarden, KeePass, and Keeper and I think you'll quickly make an assessment. Even if you don't understand a single technical detail, you should notice a difference in openness and comprehensiveness.
I searched for security audits for my old password manager and couldn't find anything. Red flag.
I searched for audit information for another popular commercial password manager and also couldn't find a single published security audit. Red flag.
5. SOC 2 Certification
I know very little about SOC Certification, but I found that 1Password and BitWarden both provide information about their SOC Certifications. Keeper mentions SOC 2 compliance, but does not appear to have a dedicated page for their certification.
BitWarden touts both SOC 2 and SOC 3 Certifications, but according to this blog post, it seems that SOC 2 Certification is more comprehensive, and is the one that matters, of the two.
I was unable to find any mention of SOC Certification for my old password manager or another popular password manager.
I cannot yet assess the actual value of the SOC 2 Certification, but I'm assuming it's a costly process that companies undertake in order to actually improve their security posture, and not a perfunctory "vanity audit".
Things Change
Just because you find a password manager that meets your needs and satisfies your security criteria today, I would not make it your "forever" password manager. Assume that you will need to re-evaluate your password manager in 1-4 years to confirm it's still a good choice, and see if another option might better fit your criteria.
My old password manager was a #1 "Editor's Choice" pick when I started using it in 2008. It clearly has not kept up with the increasing security risks in 2022.
If my new password manager stops doing audits and penetration tests in 2 years, I may need to find a new solution. It's a hassle to change password managers, but I now recognize that I can't assume that my data will be kept safe indefinitely in a particular password manager.
And I need to be aware of changes related to password management security. If new risks are found in AES that require a change to my master password or encryption settings, I'll need to be aware of that, and be open to potential hassle of having to change my encryption settings. If new security guidelines are release that recommend a new key derivation process, I may need to re-encrypt my vault based on new settings. Hopefully my password manager informs me of these changes.
Steve Endow is a Microsoft MVP in Los Angeles. He works with Dynamics 365 Business Central and related technologies.
You can also find him on Twitter and YouTube, or through these links: links.steveendow.com

No comments:
Post a Comment
All comments must be reviewed and approved before being published. Your comment will not appear immediately.